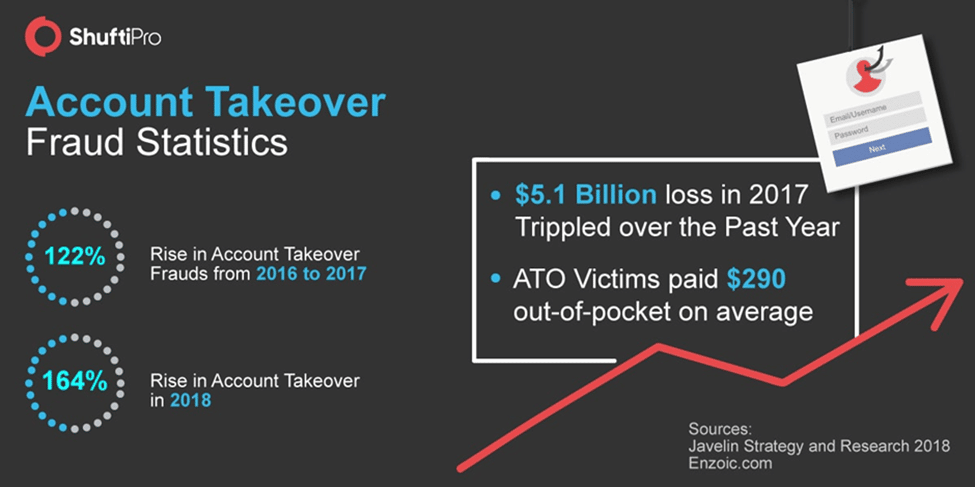
Account takeover (ATO) is the most widespread and costly assault against banking institutions, eCommerce businesses, and several other companies. According to Javelin Strategy and Research’s 2021 Identity Fraud Study, overall ATO fraud losses in 2020 exceeded $56 billion.
What is the difficulty? Consumers want more digital services and convenience, but many are not using a US VPN service. Therefore, balancing a seamless customer experience and security against ATO and other fraudulent schemes is necessary. Let us first understand what exactly ATO is.
What do you mean by ATO
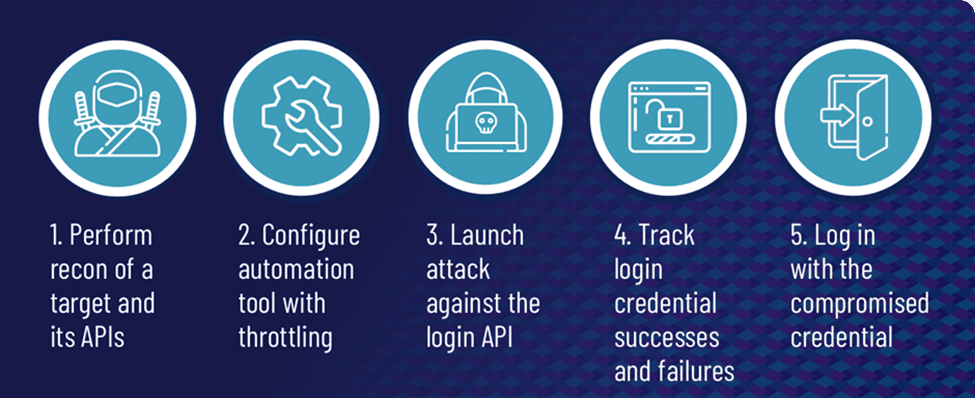
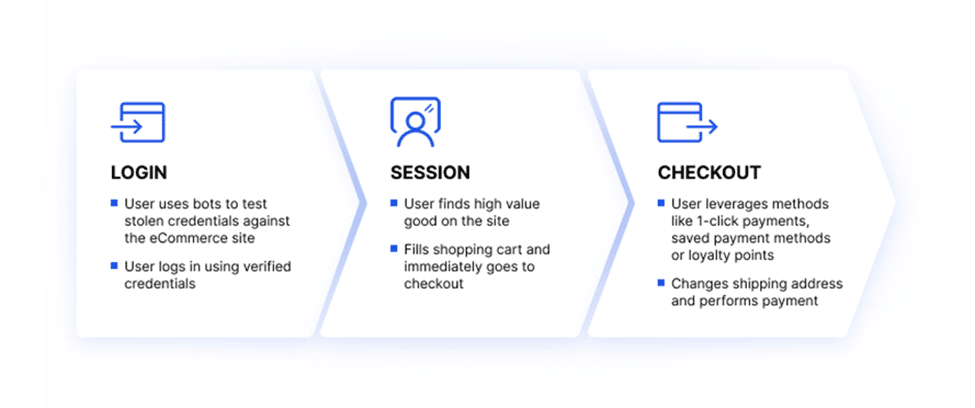
ATO is an attack in which hackers use stolen passwords and usernames to seize control internet accounts. Typically, cybercriminals get a list of credentials on the dark web; these credentials are obtained through social engineering, data breaches and phishing attempts. They utilize these credentials to deploy bots that automatically access travel, retail, financial, e-commerce, and social networking sites to test password and username combinations and log in.
Eventually, attackers amass a list of validated credentials and earn by selling them to other individuals or misusing the account. ATO attacks are a type of identity theft.
Users seldom change their passwords and frequently reuse login information across many sites. Using bots, attackers often execute credential stuffing and brute force attacks by cycling through several passwords and username combinations to get account access.
Cybercriminals potentially compromise the login verification pages of mobile websites, websites, and APIs for native mobile applications. After gaining access, hackers commit ATO abuse and fraud, such as utilizing a user’s loyalty points.
How do ATO scams occur
The following are top five attack vectors for ATOs:
1. Theft of login information via a data breach
Each year, billions of personal documents are accessible via data breaches. Typically, the disclosed usernames and passwords are what fraudsters need to gain control of an account. Since many users use the same usernames and passwords for several websites or services, fraudsters attempt to access other online services using the same credentials.
2. Invalidation of credentials through coercion
Cybercriminals often access your personal information by attempting multiple passwords to determine the proper one. They use bots that examine many possible password combinations to expedite the process. Eight-character passwords are broken in less than an hour using the tools now accessible to hackers.
3. Phishing for login credentials
Cybercriminals also request the login credentials of their victims. This is accomplished through phishing schemes in which victims are deceived into divulging personal information. SMS, emails, phishing websites, chat discussions, malicious phone applications, and phone calls are all viable phishing methods.
4. Theft of data by viruses and malware
Viruses and malware serve many purposes. They frequently take data from the victim’s device. Numerous viruses monitor your keystrokes while you input your passwords, while others steal your banking information by eavesdropping on your browser. Prevent all this by using antivirus software.
5. MitM (man in the middle) attacks
Before reaching a website, your internet traffic passes via several servers. If someone intercepts your communication while in transit and it isn’t encrypted, they observe everything about your Internet activity, including your login credentials. Typically, man-in-the-middle assaults are conducted using home Internet routers or public Wi-Fi networks. Protect yourself with dependable VPN software.
ATO Defence
Are you wondering how to prevent ATO? ATO is the most common and expensive assault on banking, e-commerce, and other companies. Making the right management decision regarding ATO defence helps the decision-makers relax and concentrate on other essential tasks.
Top 6 ATO defence practices
Here are the top six methods for protecting your organization against ATO.
1. Multiple authentication factors
Ask your user to authenticate using anything other than their password. It requires two-factor authentication when a user attempts to access their account using a unique login device or from an unusual location. The user has to authenticate anything right from their mother’s name, the name of their first school or any item they own, such as a dongle, token etc. and something like a facial ID, iris scan or fingerprint.
2. Account monitoring software
When an account is hacked, a protocol has to be in place to prevent subsequent assaults. By placing a suspect account in a sandbox, examine all associated activity and suspend the account if necessary.
3. AI-based detection
Protection and detection systems based on AI identify increasingly complex ATO and bot assaults. ATO efforts frequently employ fourth-generation bots that easily imitate human behavior, making them more challenging to distinguish. Advanced AI-based technology is required to identify complex ATO attempts and monitor a site for suspicious activity.
4. Firewall for web application (WAF)
By filtering HTTP traffic, a Web Application Firewall (WAF) safeguards web applications. WAFs identify and prevent malicious traffic, assisting in mitigating ATO attacks using one or more of the following means:
5. Detecting and blocking known attacker requests
Identify malicious bots employed by attackers as part of ATO assaults.
6. Determine instances of credential stuffing on login portals
Detect and prevent brute force attacks by recognizing sessions that pass an abnormally large number of credentials.
Enabling multi-factor authentication (MFA) or authentication using third-party identity providers such as Google Scan traffic for “fingerprints” that indicate credential stuffing tools
How to safeguard yourself against ATO scams
Educating your users and workers on the value of their accounts is an excellent first step in making life more difficult for fraudsters since this alters their behavior toward protecting account access.
You have to use common sense but also make a concerted effort to remind others to
- Stop reusing passwords. Several negative repercussions are associated with losing a single account. The loss of all internet accounts is catastrophic.
- Change passwords frequently. This helps safeguard accounts from data breaches in the past.
- Use password managers. These build robust passwords, store them in a secure location, and autofill them on websites and applications as necessary.
- Be cautious with links, particularly from unknown email senders, poorly written material, or questionable websites. Enter key websites straight into your browser instead of tapping on links.
- Verify the URLs. Be wary of phishing attempts if the URL or web page appears odd, particularly when inputting credentials or personal information, for example, www.paypall.com.
- Enable MFA. Thanks to third-party programs like Google Authenticator, two-step verification (2SV) or two-factor authentication (2FA) are easier to use than ever. Especially when connecting to public WiFi networks, use a VPN.
- Screenshot for reporting account fraud. You also have to be transparent with your users about the dangers associated with ATO and keep them routinely informed of any account-affecting changes.
For instance, use a confirmation email to inform the client that a new phone number has been registered or to confirm their previous chat with a customer care agent.
- pwned passwords: Verify whether your password(s) have been compromised at have I been pwned website.
How to boost your protection against ATO scams?
As a firm, it is essential to adhere to the finest data protection procedures applied to all collected, transmitted, processed, and accessed information. Included in a non-exhaustive list of examples are:
- Use SSL- For pages that collect sensitive or personally identifiable information like credit card details, social security numbers, and addresses, check for any SSL interception.
- Utilize encryption– It has to be used wherever possible, not only for authentication but also for communications.
This is especially critical for workplace phones, laptops, and desktop PCs, particularly in a work-from-home environment.
- Employ ethical (white hat) hackers- For instance, Facebook offers a bug bounty program that awards up to $40,000 to independent researchers like white hat hackers who discover flaws that often lead to ATO.
- Check user passwords twice- Utilize third-party services, such as Troy Hunt’s Pwned Passwords2 or K-Anonymity if you’re a Cloudflare subscriber, to determine if a user’s credentials have been stolen previously. This is handy for alerting your users at registration if they are about to use a leaked password or trigger an email verification on logins to ensure they aren’t ATO victims.
- Restrict user input- This includes restricting HTML input, sanitizing data entered, and using Allowlists to guarantee that your site code is clean and not susceptible to SQL or HTML injection attacks.
- Consider user friction- In a perfect world, implement as many authentications and verification stages as necessary to confirm that your users are who they declare to be.
In practice, however, these processes pose significant difficulties for your customers and result in a negative user experience. Especially in today’s always-on economy, increasing friction during registration or login is the surest way to drive users to the more accommodating competition.
So how do you strike the perfect balance between security and consumer friction? By implementing stealthy authentication mechanisms.
If your anti-fraud solutions enable you to regulate the thresholds between what is acceptable and what requires further inquiry, it is much simpler to provide a seamless authentication experience.

About Author – Fatema Aliasgar is an experienced B2B and SaaS content writer based in Mumbai, India. She has done her Master’s in Business Management and has written B2B content for seven years. She likes to read non-fiction and play board games with her kids during her free time.